Identity Provider Settings
This reference covers all of Pomerium's Identity Provider Settings:
- Identity Provider Client ID
- Identity Provider Client Secret
- Identity Provider Client Secret File
- Identity Provider Name
- Identity Provider Request Params
- Identity Provider Scopes
- Identity Provider URL
- Identity Provider Polling Min/Max Delay
Pomerium uses the Hosted Authenticate Service by default.
If you want to run Pomerium with a self-hosted authenticate service, include an identity provider and authenticate service URL in your configuration.
See Self-Hosted Authenticate Service for more information.
Supported identity providers
Pomerium supports all major single-sign on (SSO) identity providers. See the identity providers page for a list of supported SSO providers and guides to integrate each provider with Pomerium.
Pomerium can also integrate with any identity provider that supports OAuth 2.0 and OIDC protocols.
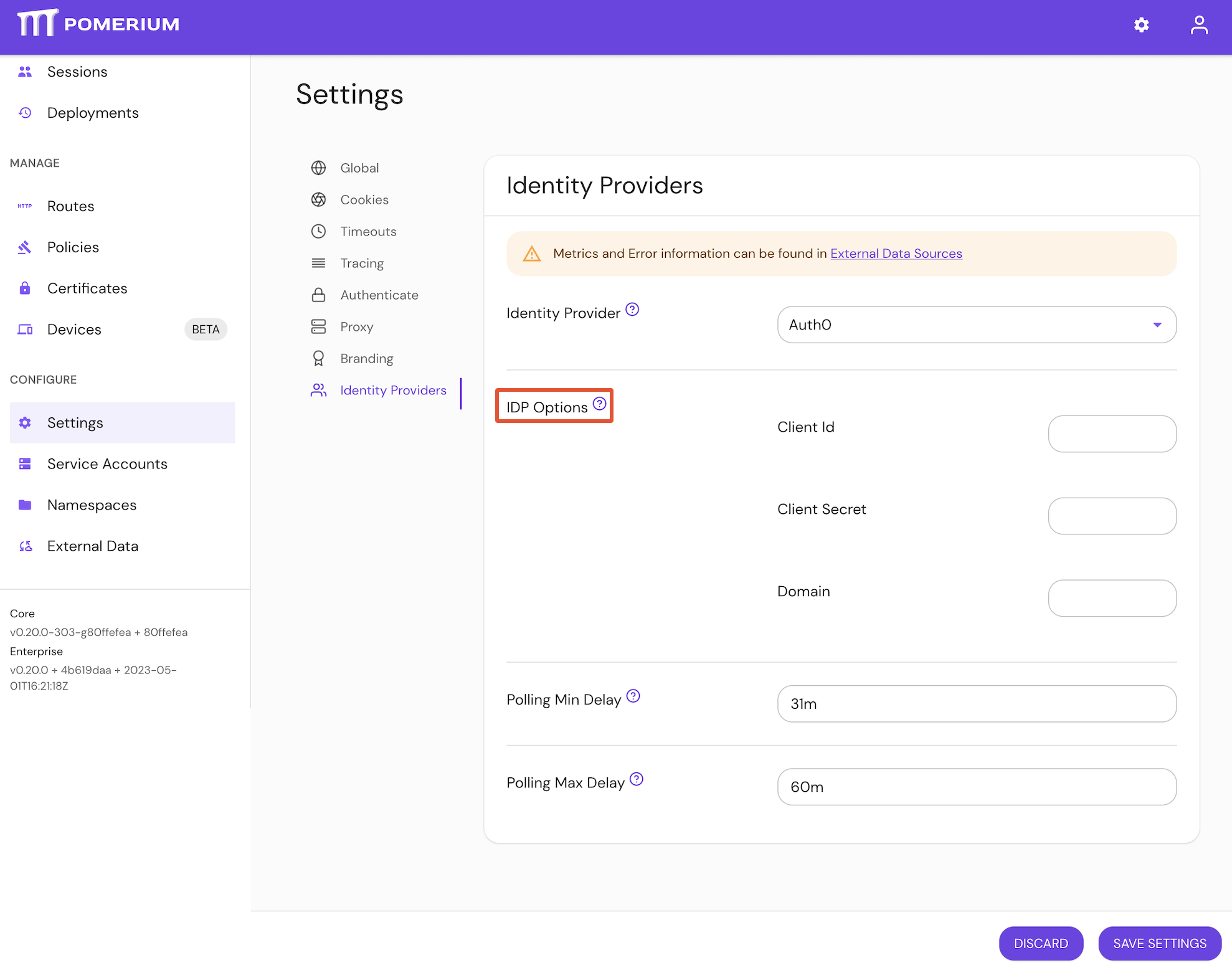
Identity Provider Client ID
Identity Provider Client ID is the OAuth 2.0 Client Identifier retrieved from your identity provider. See your identity provider's documentation, and Pomerium's identity provider docs for details.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_client_id | IDP_CLIENT_ID | string | required (if self-hosting) |
Configure Identity Provider Client ID under IDP Options in the Console:
Examples
# config file key
idp_client_id: idp_client_id
# environment variable
IDP_CLIENT_ID=idp_client_id
Identity Provider Client Secret
Identity Provider Client Secret is the OAuth 2.0 Secret Identifier retrieved from your identity provider. See your identity provider's documentation, and Pomerium's identity provider docs for details.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_client_secret | IDP_CLIENT_SECRET | string | required (unless using idp_client_secret_file) |
Configure Identity Provider Client Secret under IDP Settings in the Console:

See identityProvider.secret for more information
Examples
# config file key
idp_client_secret: idp_client_secret
# environment variable
IDP_CLIENT_SECRET=idp_client_secret
Identity Provider Client Secret File
Identity Provider Client Secret File is the OAuth 2.0 Secret Identifier retrieved from your identity provider. See your identity provider's documentation, and Pomerium's identity provider docs for details.
The identity provider client secret file points to a file containing the secret. This is useful when deploying in environments that provide secret management like Docker Swarm.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_client_secret_file | IDP_CLIENT_SECRET_FILE | string | required (unless using identity_provider_client_secret) |
idp_client_secret_file is a bootstrap configuration setting and is not configurable in the Console.
See identityProvider.secret for more information.
Examples
# config file key
idp_client_secret_file: '/run/secrets/POMERIUM_CLIENT_SECRET'
# environment variable
IDP_CLIENT_SECRET_FILE='/run/secrets/POMERIUM_CLIENT_SECRET'
Identity Provider Name
Identity Provider Name is the short-hand name of a built-in OpenID Connect (OIDC) identity provider used for authentication.
See identity provider for details.
The supported values for this setting are:
appleauth0azurecognitogithubgitlabgoogleoidcoktaoneloginping
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_provider | IDP_PROVIDER | string | required (if self-hosting) |
Set Identity Provider Name under the Identity Provider options in the Console:
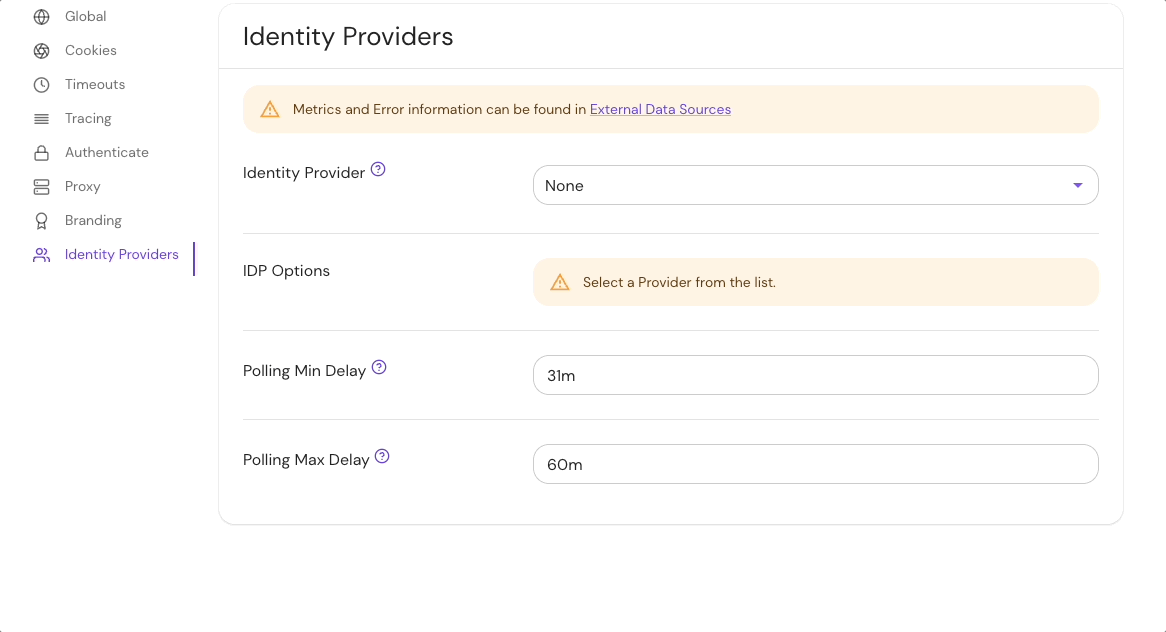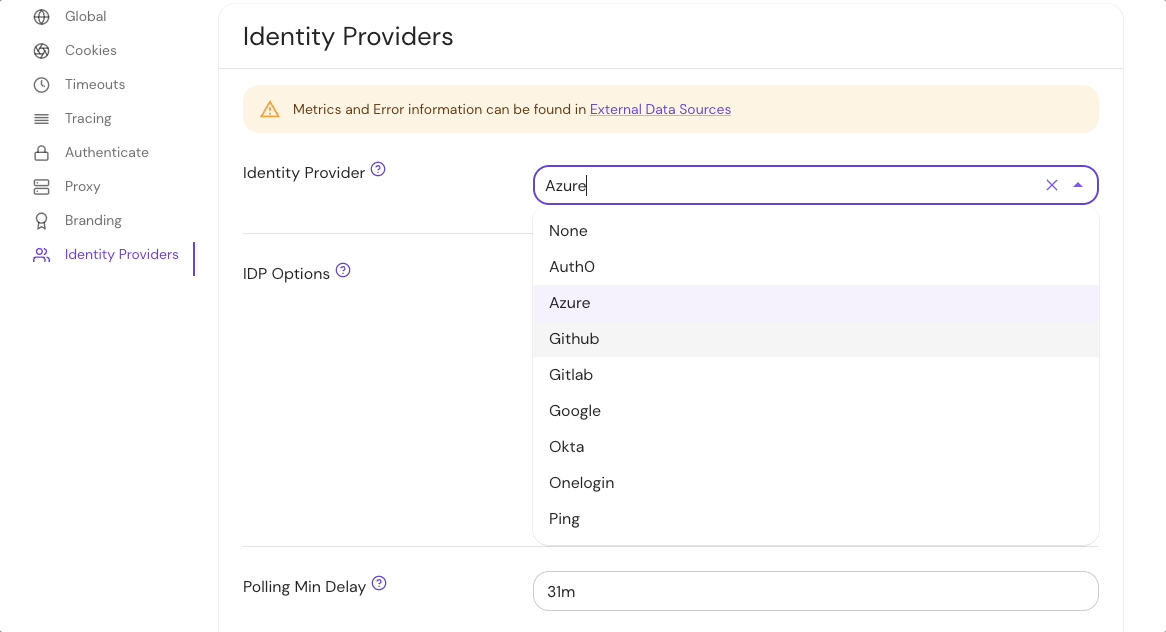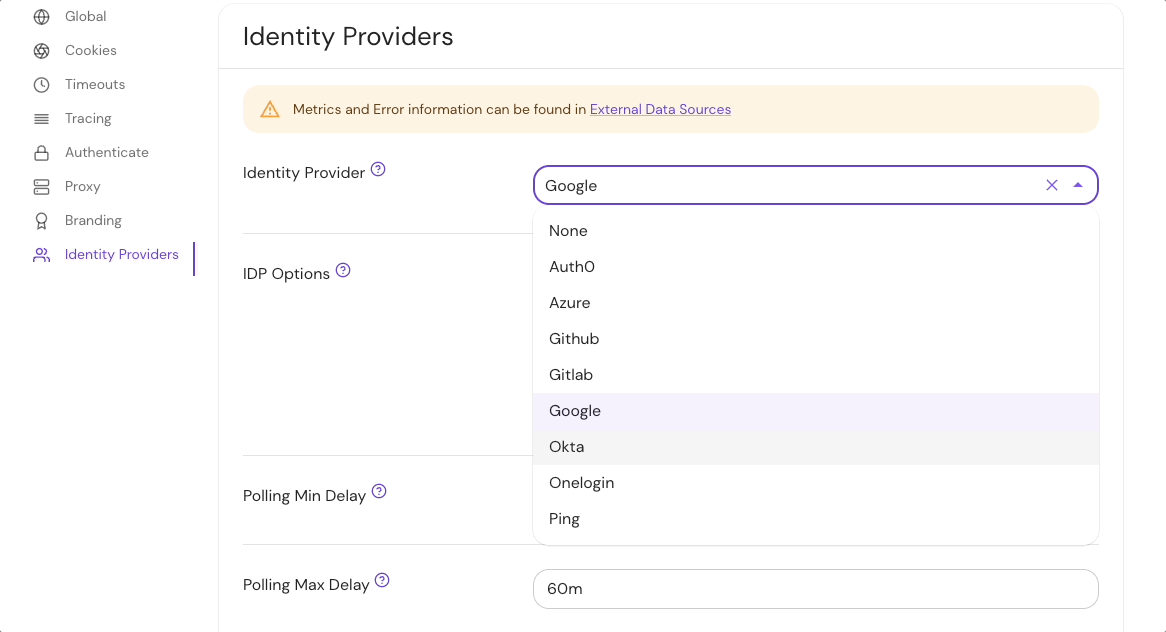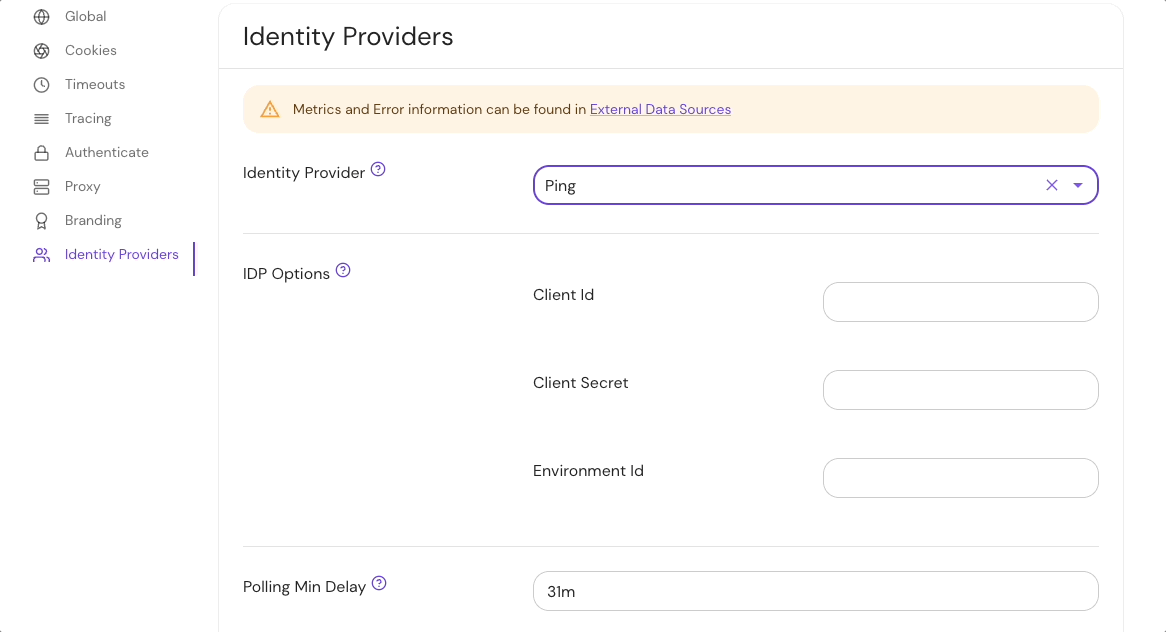
See identityProvider.provider for more information
Examples
# config file key
idp_provider: auth0
# environment variable
IDP_PROVIDER=github
Identity Provider Request Params
Identity Provider Request Params lists the parameters you want to include as part of a sign-in request using the OAuth 2.0 code flow.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_request_params | n/a | string (map of key-value pairs) | optional |
Configure Identity Provider Request Params under Authenticate settings in the Console:
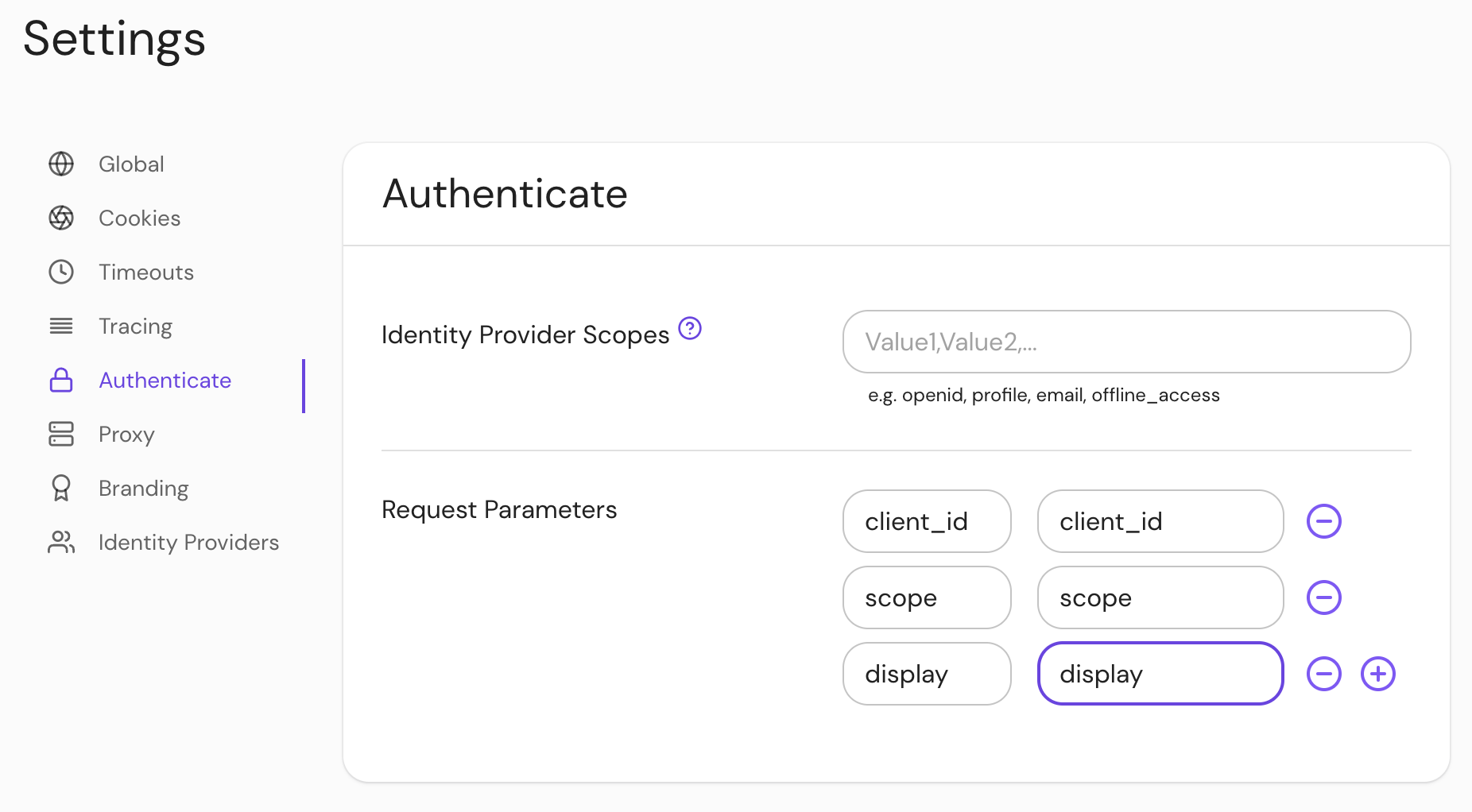
See Kubernetes identityProvider.requestParams and identityProvider.requestParamsSecret for more information
Defaults
Pomerium includes some default parameters for specific identity providers. Setting this configuration option will replace these default parameters. To remove the default parameters entirely, set this option to an empty map* (e.g. idp_request_params: {} in the config file).
| Provider | Default parameters |
|---|---|
apple* | |
azure | |
google | |
*The default parameters for apple behave differently; any values set using this configuration option will be merged with the default parameters.
Examples
# config file key
idp_request_params:
client_id: client_id
response_type: response_type
redirect_uri: redirect_uri
For more information, see:
- OIDC Request Parameters
- IANA OAuth Parameters
- Microsoft Azure Request params
- Google Authentication URI parameters
Identity Provider Scopes
Identity Provider Scopes correspond to access privilege scopes as defined in Section 3.3 of OAuth 2.0 RFC6749.
The scopes associated with Access Tokens determine what resources will be available when they are used to access OAuth 2.0 protected endpoints.
If you are using a built-in provider, you probably don't want to set customized scopes.
Some providers, like Amazon Cognito, do not support the offline_access scope.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_scopes | IDP_SCOPES | string (list) | optional (for built-in identity providers) |
Configure Identity Provider Scopes under Authenticate settings in the Console:
See Kubernetes identityProvider.scopes for more information
Defaults
| Defaults |
|---|
openid |
profile |
email |
offline_access |
Examples
# config file key
idp_scopes: openid, profile, offline_access, email
# environment variable
IDP_SCOPES=openid, profile, offline_access, email
Identity Provider URL
Identity Provider URL is the base path to an identity provider's OpenID connect discovery document. An example Azure URL would be https://login.microsoftonline.com/common/v2.0 for their discovery document.
"Base path" is defined as the section of the URL to the discovery document up to (but not including) /.well-known/openid-configuration.
How to configure
- Core
- Enterprise
- Kubernetes
| Config file keys | Environment variables | Type | Usage |
|---|---|---|---|
idp_provider_url | IDP_PROVIDER_URL | string | required (depending on identity provider) |
Set the Identity Provider URL under IDP Options settings in the Console:

See Kubernetes identityProvider.url for more information
Examples
# config file key
idp_provider_url: 'https://awesome-company.auth0.com'
# environment variable
IDP_PROVIDER_URL='https://awesome-company.auth0.com'
Identity Provider Polling Min/Max Delay
Identity provider Polling Minimum Delay and Polling Maximum Delay settings define the minimum and maximum delay times between requests to the identity provider data source.
A job starts with the minimum delay intervals. If the job fails to complete within the minimum delay period, it will be interrupted and the job will restart. If the job is interrupted due to timeout or an error, it will restart with increasing intervals up to the maximum delay period.
How to configure
Set the Identity Provider Max/Min Delay settings in the Console:
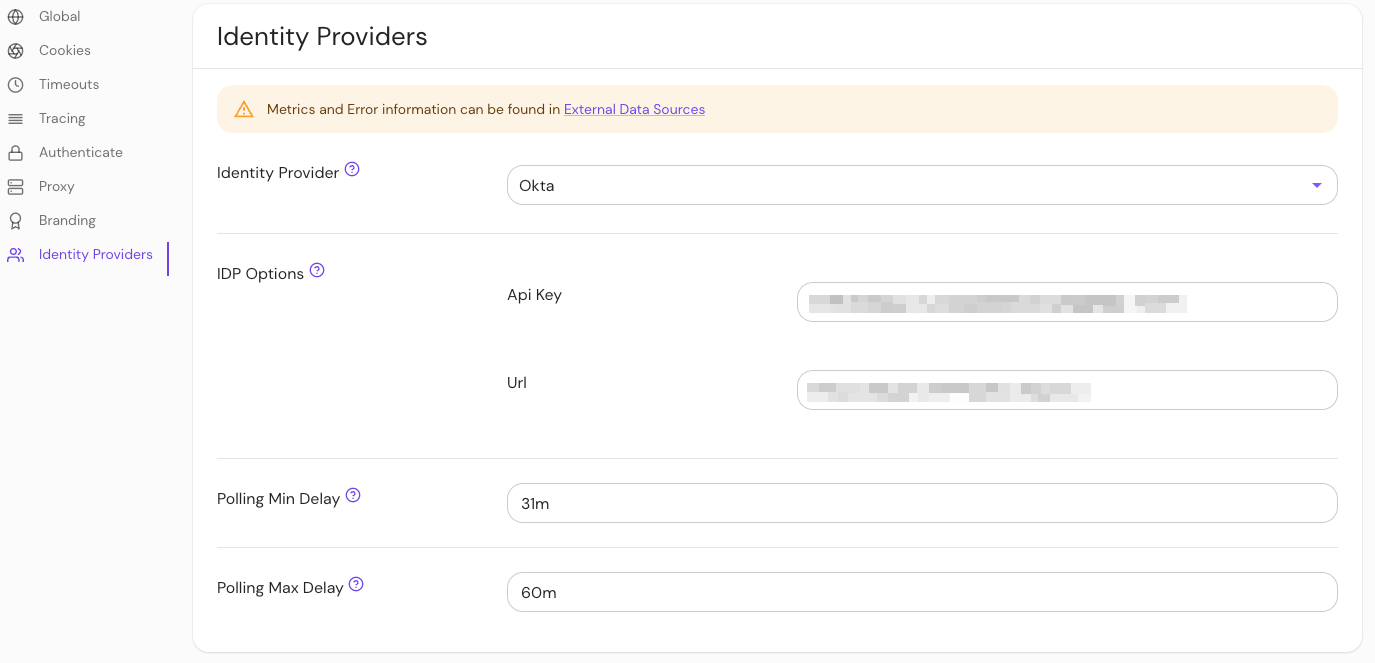
The minimum_delay and maximum_delay settings are an Enterprise Console feature, and are not configurable in Pomerium Core.
Defaults
While minimum and maximum polling time defaults are set for any Console installation, the required durations will vary depending on your identity provider and the size or your organization's directory.
If the job fails before completing, increase the minimum and maximum durations until the job completes.
Keep in mind that large directories may take several hours to complete.
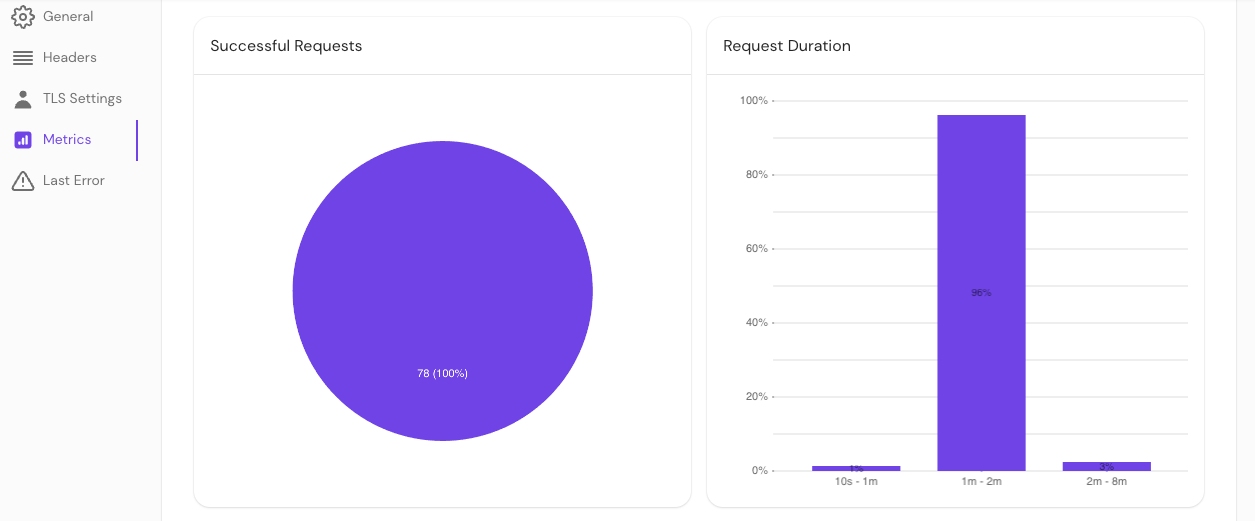
Monitor directory sync
To determine the appropriate durations required to sync your directory, check your Console logs and the Last Error and Request Duration sections of the Console GUI.
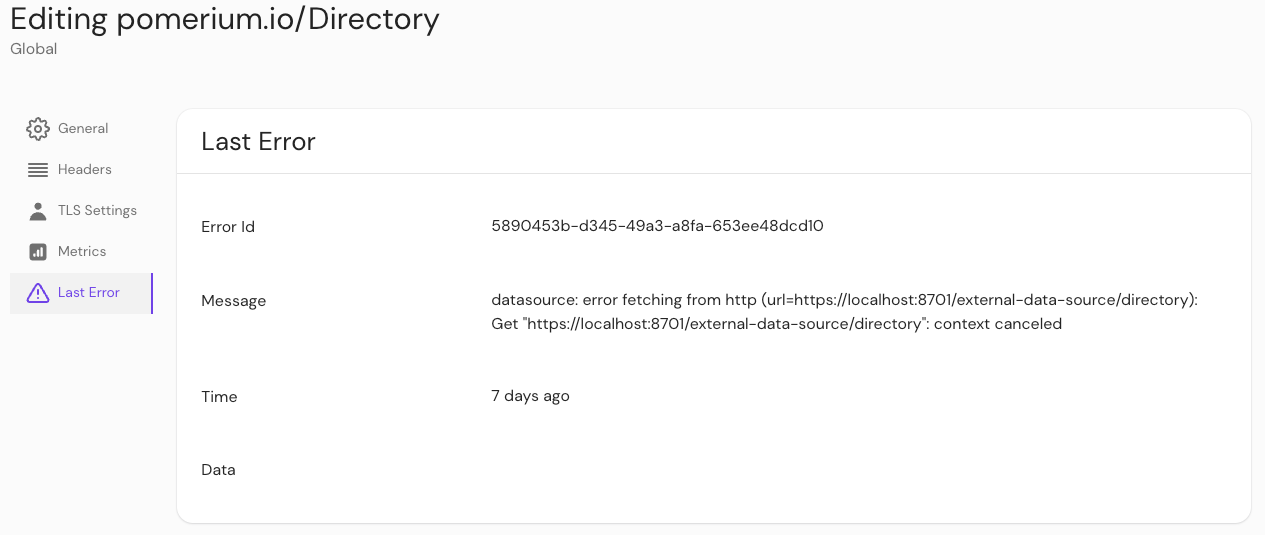
Last error
You can check if an error interrupted a job by checking External Data > Last Error.
Request duration
You can also check External Data > Metrics to view request durations.